2023 Cloud-Native Security Trends and Insights
Enhance cloud-native security with Zero Trust, DevSecOps, and AI-driven tools. Learn key practices for secure, compliant environments

Cloud-native security is a constantly evolving landscape, and staying up-to-date with the latest trends and best practices is essential. By adopting a Zero Trust security model, integrating security into the DevOps process, using cloud security posture management tools, leveraging AI and ML, implementing multi-cloud security solutions, and investing in IAM, compliance, threat intelligence, security automation, and security awareness training, organizations can ensure their cloud-native environments are secure and compliant.
As cloud computing continues to dominate the IT landscape, cloud security has emerged as a critical area of focus for organizations worldwide. The ever-evolving nature of cloud technologies and the increasing sophistication of cyberattacks demand a proactive approach to cloud security. In this blog post, we’ll explore the key cloud-native security trends that organizations must be aware of in 2023 to effectively safeguard their cloud environments.
Zero Trust Architecture (ZTA)
Zero Trust Architecture (ZTA) is a security model that assumes no user or device is trusted by default, regardless of their location or identity. This means that all users and devices must be verified before they are granted access to cloud resources, even if they are within the organization’s network. ZTA is a departure from traditional perimeter-based security models, which focus on protecting the perimeter of the network and assume that users and devices within the perimeter are trusted.
Security Service Edge (SASE)
Security Service Edge (SASE) is a cloud-based security architecture that combines network security, cloud access security broker (CASB), and other security functions into a single service. SASE provides organizations with a unified view of their cloud security posture and enables them to enforce security policies consistently across all cloud environments.
Cloud-Native Security Tools
Cloud-native security tools are designed to be deployed and managed in the cloud. These tools are often more scalable and flexible than traditional security tools, making them better suited for the dynamic and distributed nature of cloud environments. Cloud-native security tools provide organizations with real-time visibility into their cloud environments and enable them to quickly detect and respond to security threats.
Data Security
Data security is the process of protecting data from unauthorized access, use, disclosure, disruption, modification, or destruction. Data security is becoming increasingly important as businesses store more and more sensitive data in the cloud. Organizations must implement robust data security measures to protect their data from a wide range of threats, including data breaches, ransomware attacks, and insider threats.
Application Security
Application security is the process of protecting applications from vulnerabilities that could be exploited by attackers. Application security is becoming increasingly important as businesses move more of their applications to the cloud. Organizations must implement a comprehensive application security program to identify, remediate, and prevent vulnerabilities in their cloud applications.
Compliance
Compliance is the process of ensuring that an organization’s cloud environment meets all applicable laws and regulations. Compliance is becoming increasingly important as businesses store more and more sensitive data in the cloud. Organizations must have a clear understanding of the compliance requirements that apply to their cloud environments and implement the necessary controls to meet those requirements.
Cloud Security in the Digital Age: Practical Strategies for Enhanced Protection
In addition to implementing the key cloud-native security trends discussed above, organizations can further enhance their cloud security posture by adopting the following best practices:
- Utilize resource requests and limits to prevent overprovisioning and resource contention. Leverage node-level resource allocations to optimize resource utilization and reduce waste.
- Implement horizontal pod autoscaling (HPA) to scale resources dynamically based on demand.
- Implement a resource cleanup policy to remove unused resources regularly. Implement a resource allocation policy to ensure resources are allocated efficiently based on workload requirements.
- Implement a security policy to enforce security controls and prevent unauthorized access.
- Implement a monitoring policy to gain visibility into the cloud environment and detect security threats promptly.
- Implement a backup policy to protect data from loss or corruption.
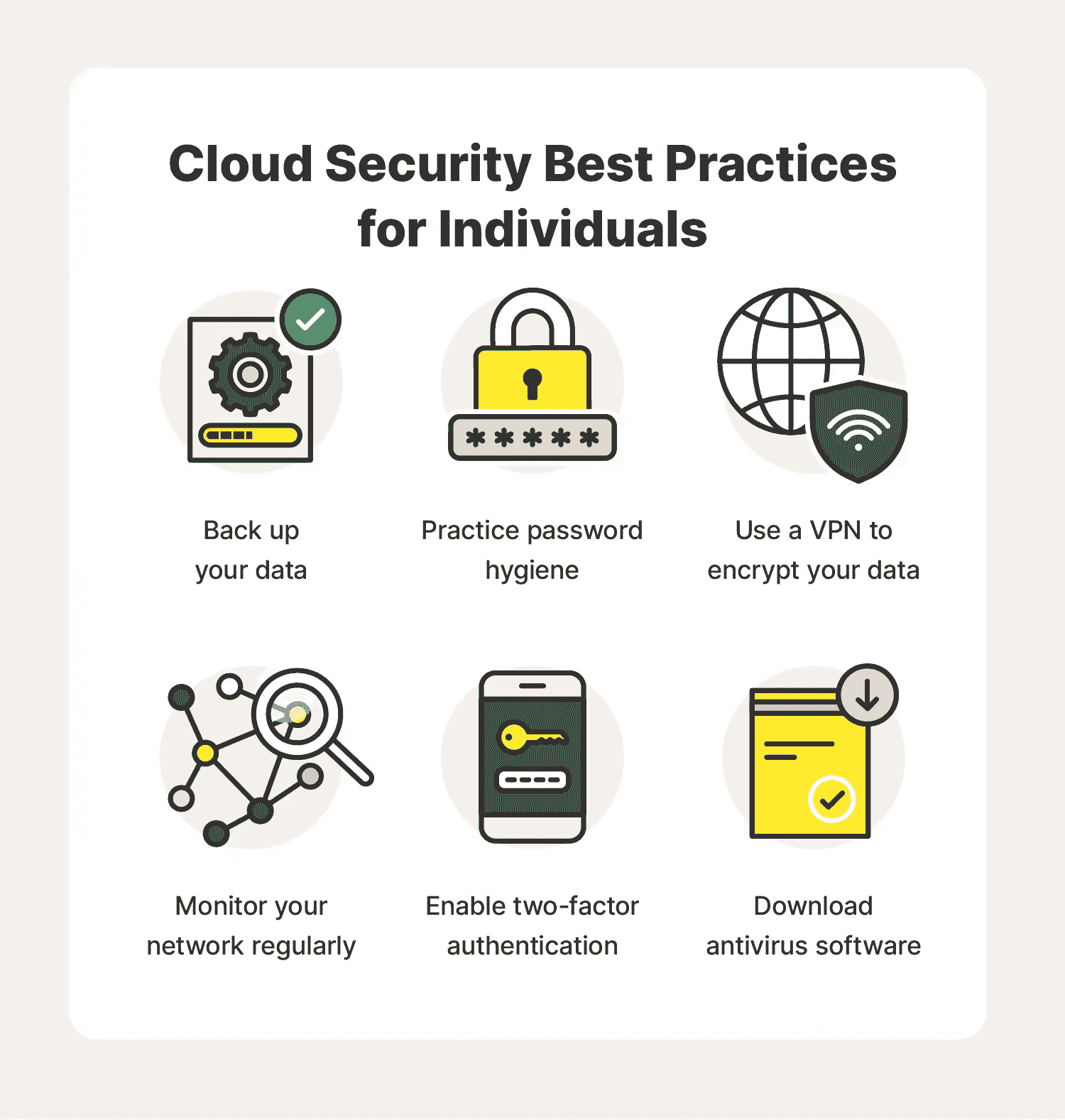
Image credit: us.norton.com
By following these best practices, organizations can significantly enhance their cloud security posture and protect their valuable data and applications from the ever-evolving threat landscape.
Conclusion
Cloud-native security trends are constantly evolving, and organizations must stay up-to-date on the latest trends to effectively protect their cloud environments. By understanding and implementing the key cloud-native security trends discussed in this blog post, organizations can safeguard their data, applications, and infrastructure from the evolving threat landscape.
Boost your Magento 2 store performance with AWS cloud infrastructure. Discover how global data centers enable faster response times.
